这道题是这次八月赛的一道200分的杂项,脑洞挺多,题目质量也好,不愧是L1near师傅出的题,i了i了
零宽字符和坚果云
首先这道题目给的信息真的非常的少,就一个txt文件,当时比赛的时候真的几乎啥也没看出来
打开txt,可以看到给了一串神秘代码

当时还以为是aes加密啥的,完全没想到居然是个网盘后缀
为什么是坚果云呢?这就涉及到这串字符中的零宽字节隐写了,当时比赛的时候我也发现了这么几个字符文件大小怎么就114字节了,但完全没想零宽字符,我太菜了┭┮﹏┭┮
使用vim就可以清晰的看得到这些零宽字符
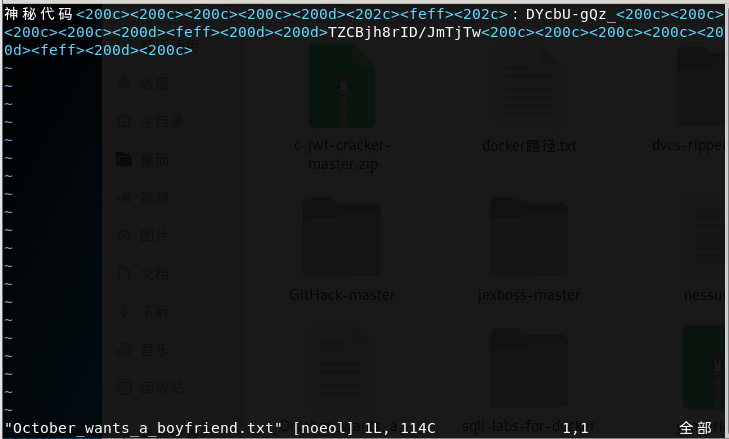
这里给出一个解码网站,将整一串字符复制过去解码,可以得到nut,也就想到了坚果云,如图
需要注意的是每个零宽字节网站解码出来的结果可能都不一样,所以比赛的时候有些师傅没解对,参考Ga1@xy’s师傅的这篇博客,这个网站也是师傅这取的
去网上找了一番坚果云的前缀,居然没找到,最后自己注册了一个,发现前缀就是jianguoyun.com/p/,emmm
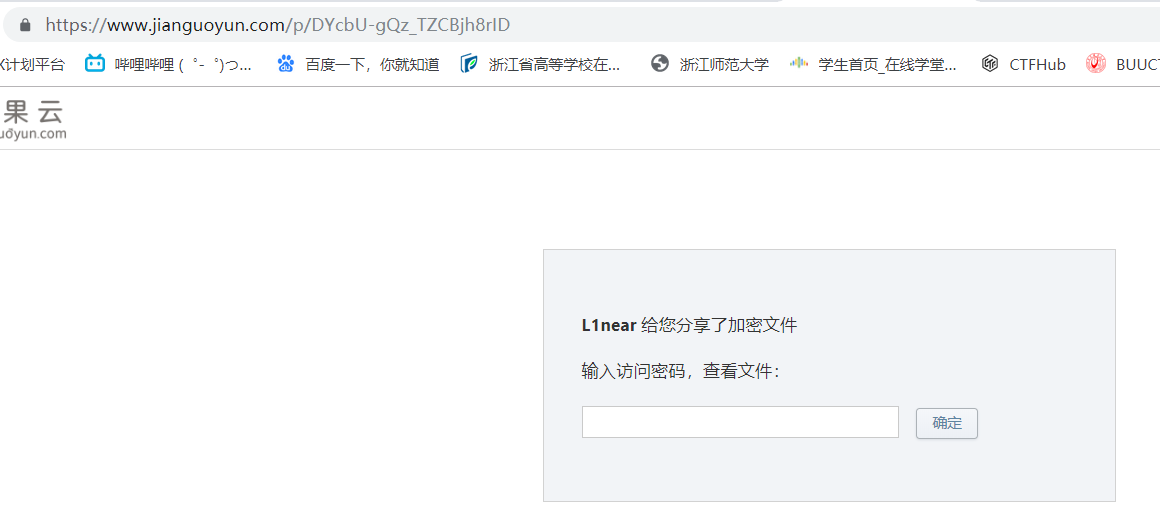
最后去这个地址可以看到是L1near师傅分享的一个文件,密码就是JmTjw到此,第一步算是告一段落
USB流量分析与键盘鼠标流量解码脚本
下载下来上面的文件后发现是两个usb的流量包,鉴于之前也没怎么做过usb的流量分析题,所以又进行了一番搜索学习
主要参考了这篇文章和fzwjscj师傅的wp
USB协议的数据部分在Leftover Capture Data域之中,在Mac和Linux下可以用tshark命令可以将 leftover capture data单独提取出来 命令如下:
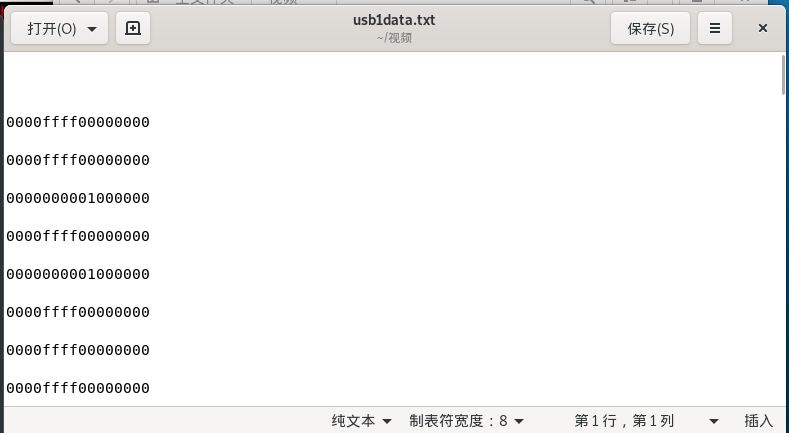
1 | tshark -r part1.pcapng -T fields -e usb.capdata > usb1data.txt |
其中part1是鼠标的,part2是键盘的,提取出来如下图
然后就是要用脚本来进行解码了,这里就直接用fzwjscj师傅写好的脚本了,直接用csdn里的那个脚本是解不出来的,要稍微修改,比赛里也提示了是1 3 5字节
1 | #!/usr/bin/env python |
这个脚本运行后得到的是一串坐标,需要用Gnuplot这个软件来绘制出图片,kali上apt安装就行,至于这个软件怎么用可以看看这篇文章
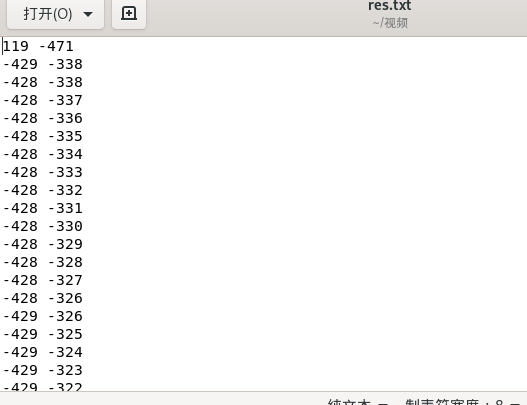
这里用到的命令是
>plot “res.txt” using 1:2
*以第一列为x轴,第二列为y轴,绘制二维数据图
得到一张上下镜像的图,上下镜像翻转即可得到flag前半段
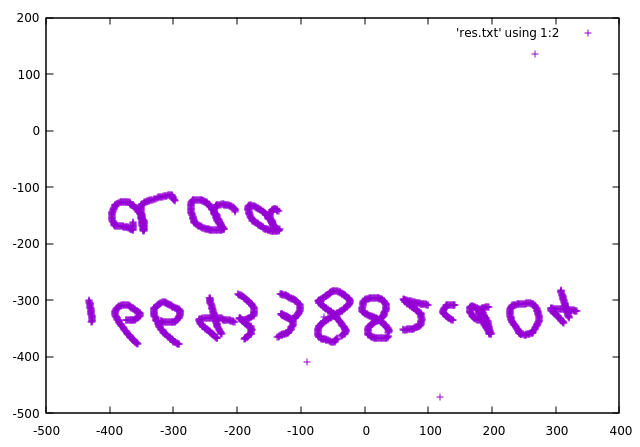
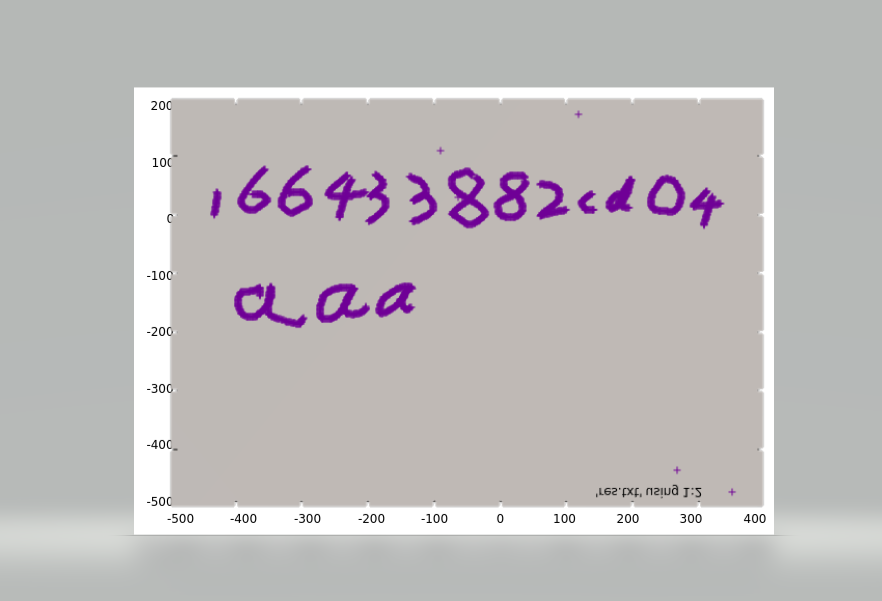
flag part1: 166433882cd04aaa
然后就是第二段了,这里也直接贴一个fzwjscj师傅的脚本
1 | #!/usr/bin/env python |
得到输出
1 | output : |
这最后还是需要一点脑洞,根据part1又16位,part2应该也有16位,已知的9位以及35个F2,F3,以可知道5个F2,F3为一个字符,所以位培根密码,F2是a,F3是b,最后解码即可
flag part2:056bd4ad29bb522b
flag
flag:166433882cd04aaa056bd4ad29bb522b